‘Efail’ exploit exposes popular email encryption schemes
Security researchers identify critical issues with PGP and S/Mime protocols.
Encrypted emails guarded by common encryption tools are allegedly "susceptible to critical vulnerabilities" that would expose their content to potential hackers. Sebastian Schnizel, a computer science professor from the University of Münster called attention to the 'Efail' issue on Sunday via Twitter. He subsequently urged users of PGP/GPG and S/Mime software to disable it in their email clients.
Although further details on the encryption flaws were expected to go public by May 15th, they have leaked early. The complete paper can be accessed here. Efail is a term which describes exploitable loopholes in end-to-end encryption services. The Electronic Frontier Foundation (EFF) recently claimed that the encryption bug posed "an immediate risk" to PGP and S/Mime users, and that even ancient messages buried deep inside elaborately named folders are in danger. Such a flaw might not be a cause for concern if your private data files consist of mundane salutations and dank memes, however, for those in the public sphere -- journalists, activists, or politicians -- who depend on encryption tools to shield confidential workplace messages, the protective barrier is gone.

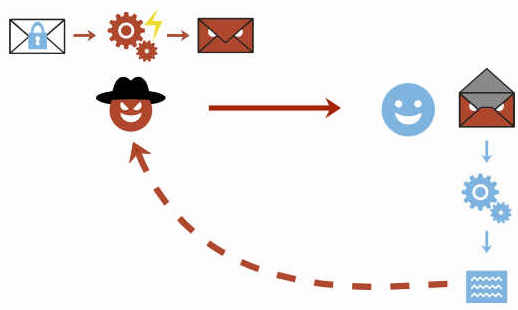
Efail attacks work by abusing the active content of HTML emails to access or 'exfiltrate' plaintext. The researchers explain that there are two main types: Direct exfiltration attacks (which target weak points in Apple Mail, iOS Mail and Mozilla Thunderbird) and CBC/CFB gadget attacks. It's this variety that attackers use to ambush users of OpenPGP and S/Mime by sending a slightly modified S/Mime email to the victim's address. By injecting malformed images or styling resources into encrypted plaintext, the attacker has a one in three chance of success at decoding the remainder of the target email.
Prior to the leak, Schnizel stated that there were "no reliable fixes", and recommended that affected users disable breached encryption software. The EFF echoed Schnizel's instruction, and advised those affected to use Signal -- a free end-to-end encryption software that's compatible with both Android and iOS devices -- until the issue has been rectified.
The Efail report lists additional steps users can take to reduce the likelihood of falling prey to encryption attacks -- namely, decrypting S/Mime and PGP outside email clients in a separate application and disabling HTML rendering altogether. But the researchers cautioned that since attacks could become increasingly sophisticated in future, strategies which bolster OpenPGP and S/Mime standards are required for a long term fix.